KazNET - Live Attacks
Threat Intelligence
& Proactive Protection
Protect your corporate network effectively and regularly receive information about who and how is trying to attack your infrastructure
The service is activated within a few hours and does not require additional effort from the client.
Who needs this and why?
For those responsible for a company's information or network security and looking to:
- Improve existing protection measures and minimize risks
- Leverage analytics to identify and demonstrate awareness of threats and attacks
- Provide data-driven reports to management in support of planned activities and budget decisions
What will you get?
- A unique TI feed with IP addresses that can be easily integrated into your firewall, increasing the number of blocked attacks by at least 25%
- Access to attack analytics from cyber sensors deployed on your perimeter, as well as global insights from across the entire cyber sensor ecosystem
How it works
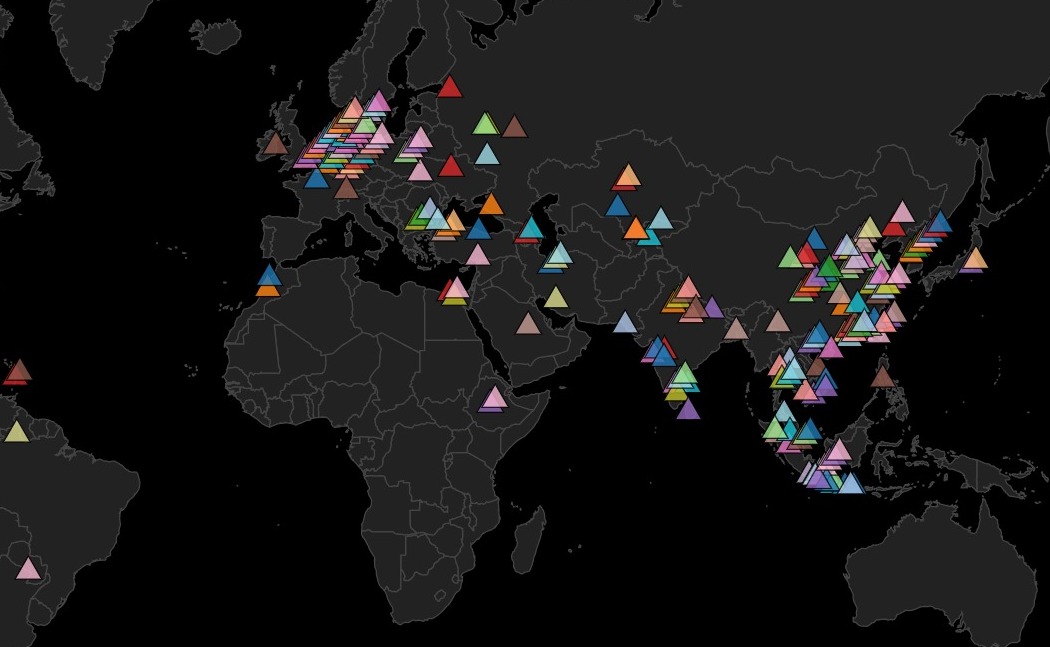
Cyber sensors
We are developing a global ecosystem of cyber sensors that detects cyberattacks at the earliest stages and transmits data to the TI platform for further analysis.
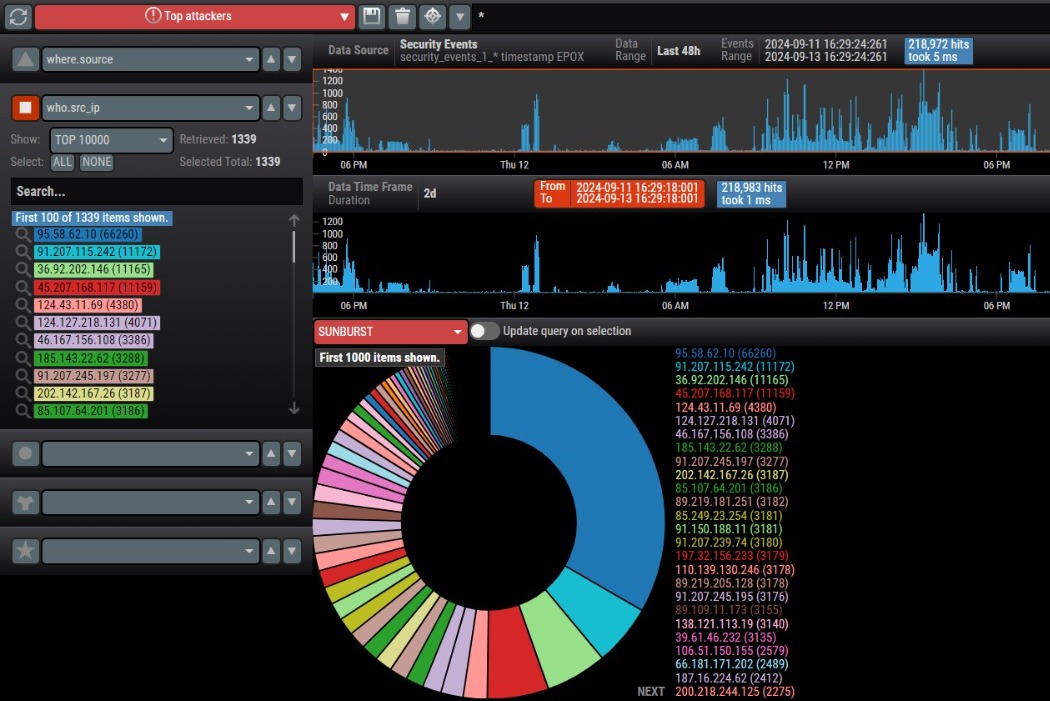
TI platform
Information about attacks is automatically processed on the TI platform in near real-time and used to generate the TI feed.
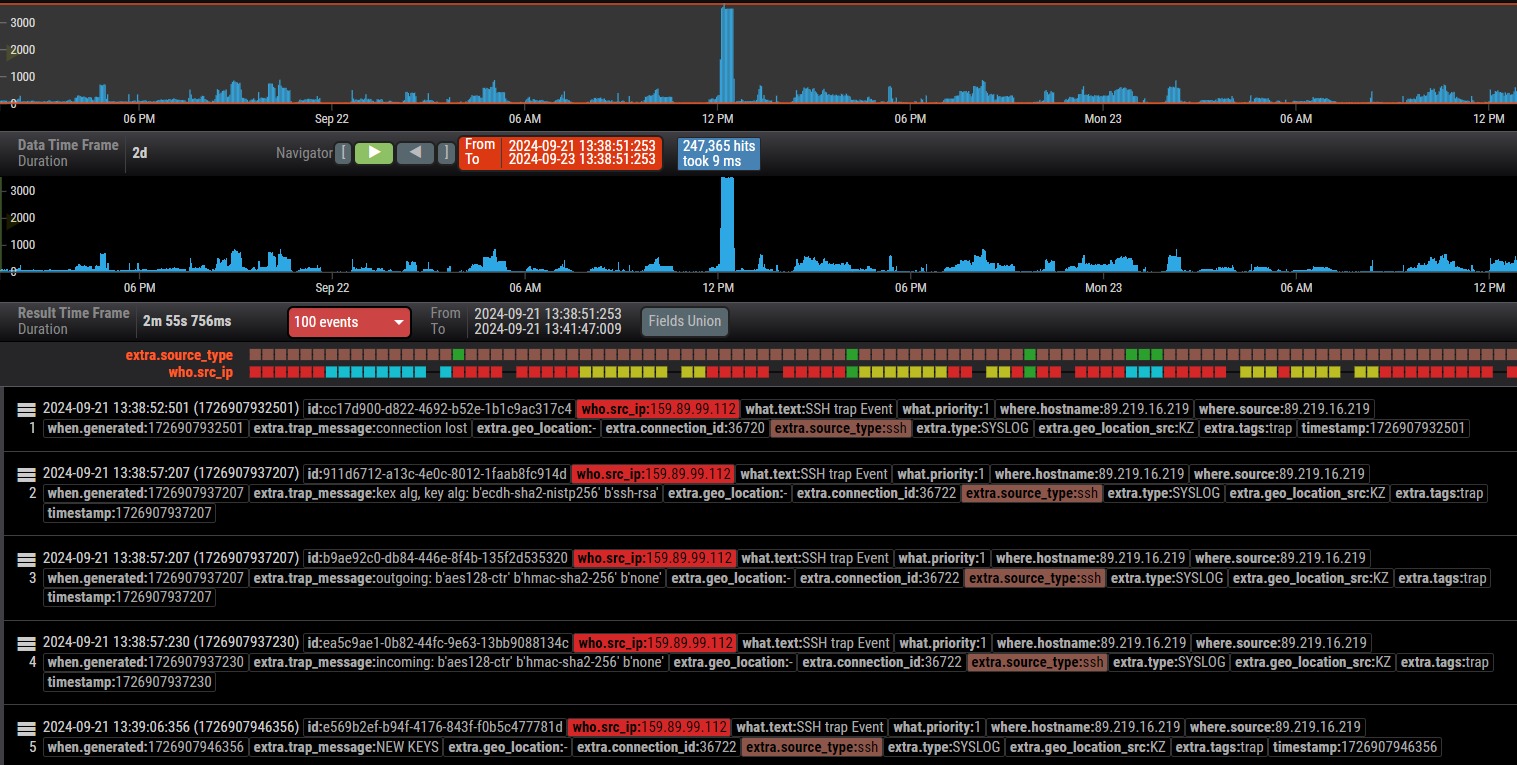
TI feed
You gain access to a unique TI feed with IP addresses that seamlessly integrates into your firewall and enhances protection.
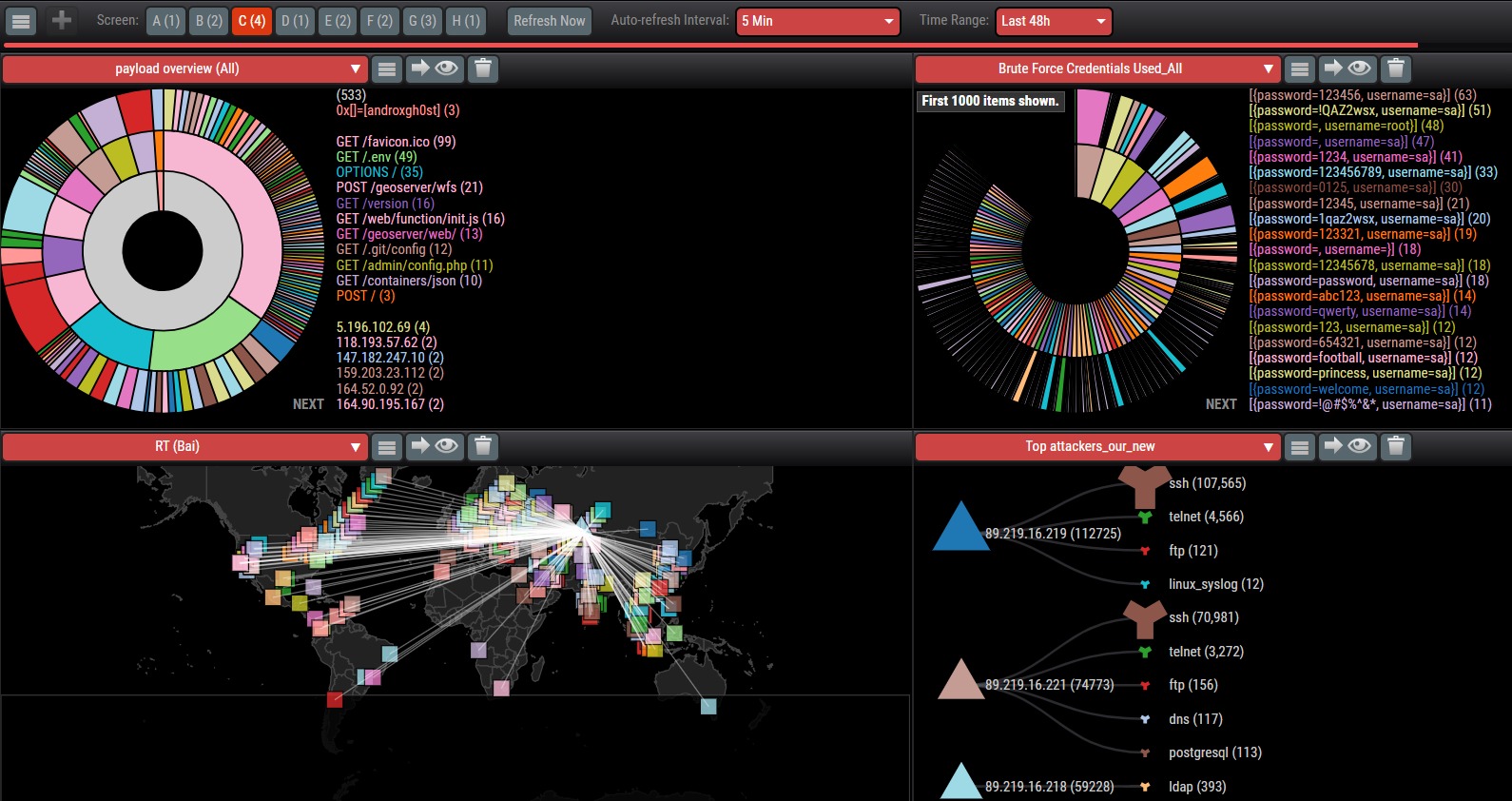
Protection
Information about attacks is collected from cyber sensors, processed on the TI platform, and made available through a user portal and expert analytics tools.
Analytics
Information about attacks is collected from cyber sensors, processed on the TI platform, and made available through a user portal and expert analytics tools.
User Portal
You will receive direct access to the user portal, featuring analytics of attacks on cyber sensors installed on your perimeter, as well as global analytics of attacks across the entire cyber sensor ecosystem.
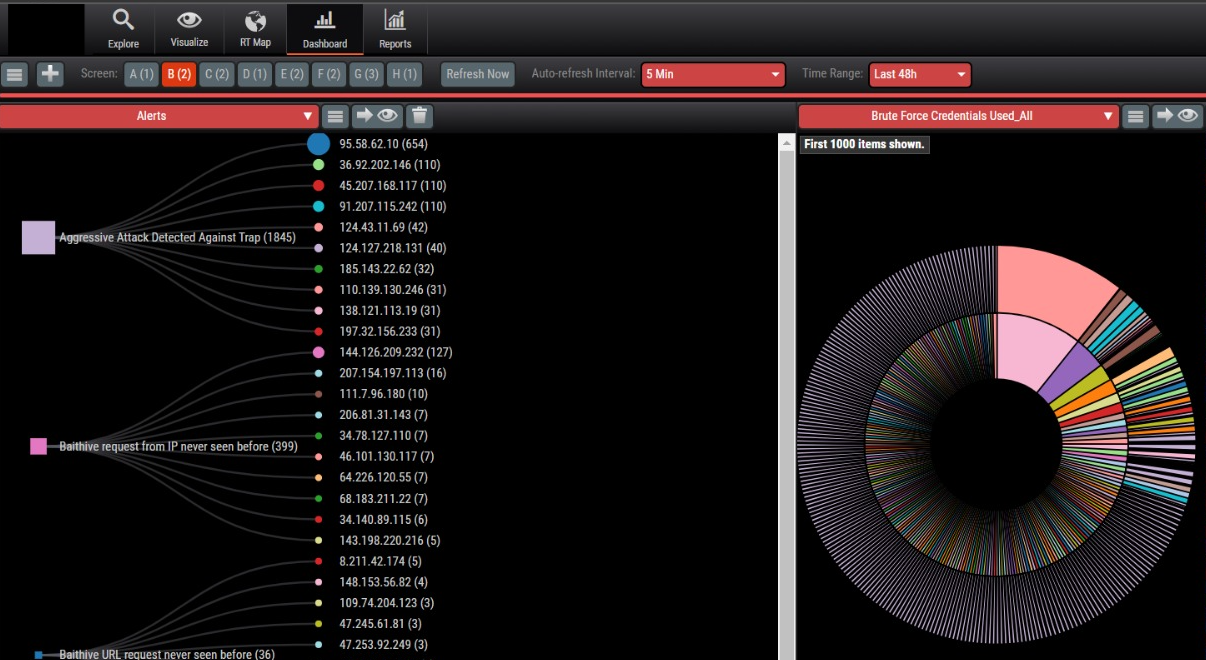
Expert analytics tools
You will get access to a specialized analytics service for conducting in-depth analysis of cyber attacks.
Why it's convenient and easy
Quick Integration
The service can be deployed in as little as one hour. Once deployed, protection becomes active immediately.
Rapid implementation
Multiple cyber sensors can be installed in just a few hours, after which attack analytics begin to be collected immediately. Within a week, the statistics begin to reflect a real picture of the actual threat landscape.
Solution on autopilot
During the pilot project — and throughout regular use — no effort is required on your side. The solution runs automatically: it protects your perimeter and continuously collects analytics on attacks targeting your network.
Seamless Rollout
If you decide to purchase our service after the pilot, all you need to do is subscribe — the entire implementation will already have been completed during the pilot phase.
Why it works
Technology
The effectiveness of our technologies has been repeatedly ...
The effectiveness of our technologies has been repeatedly confirmed by successful services in our customers' infrastructure.
Collective protection
Through the concept of Crowd Immunity, you gain ...
Through the concept of Crowd Immunity, you gain protection from threats targeting other members of the ecosystem — even before those threats can reach your own organization.
Proactive protection
Attacks are detected and blocked at the earliest ...
Attacks are detected and blocked at the earliest stages — during the initial reconnaissance and scanning for vulnerable services in your network.
Competencies as a guarantee of success
SOC
Over the past 10 years, we have accumulated extensive experience in building both internal and commercial SOCs, and we hold an active license as a Security Operations Center.
Protection
We have extensive practical experience in building cybersecurity for critical financial services in the Republic of Kazakhstan.
Incident Response
Extensive hands-on experience in countering and responding to targeted attacks and APTs against critical national infrastructure.
Project
Experienced engineers from our team will support you throughout the project until the final result is achieved.
Why it works: successful implementation examples
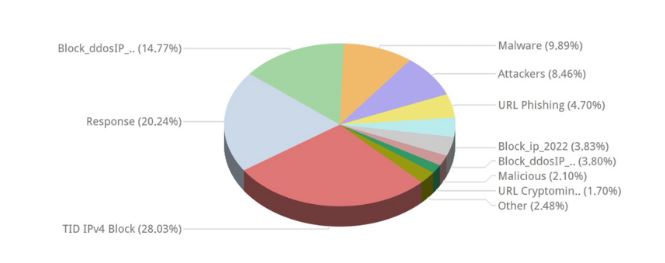
Example #1
Our threat feed accounted for 28% of all blocked attacks on the client’s NGFW, leading to an overall increase of nearly 40% in successfully prevented cyberattacks.
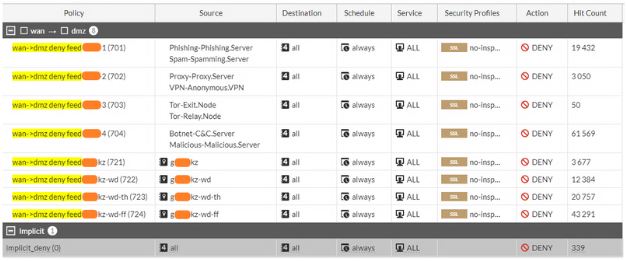
Example #2
The client's NGFW blocked 84,101 attacks using its built-in capabilities, while our TI feed enabled an additional 80,109 blocks. As a result, the total number of prevented cyberattacks increased by more than 95%!
